The Challenge
SOC analysts often face ‘alert fatigue’ switching between SIEMs, threat intel, and ticketing systems. I set out to build a unified workflow to solve this.
The Tech Stack
TheHive: For Case Management and Incident Orchestration.
Cortex: For analyzing observables (IPs, Hashes) without manual scanning.
MISP: For sharing Threat Intelligence with the community.


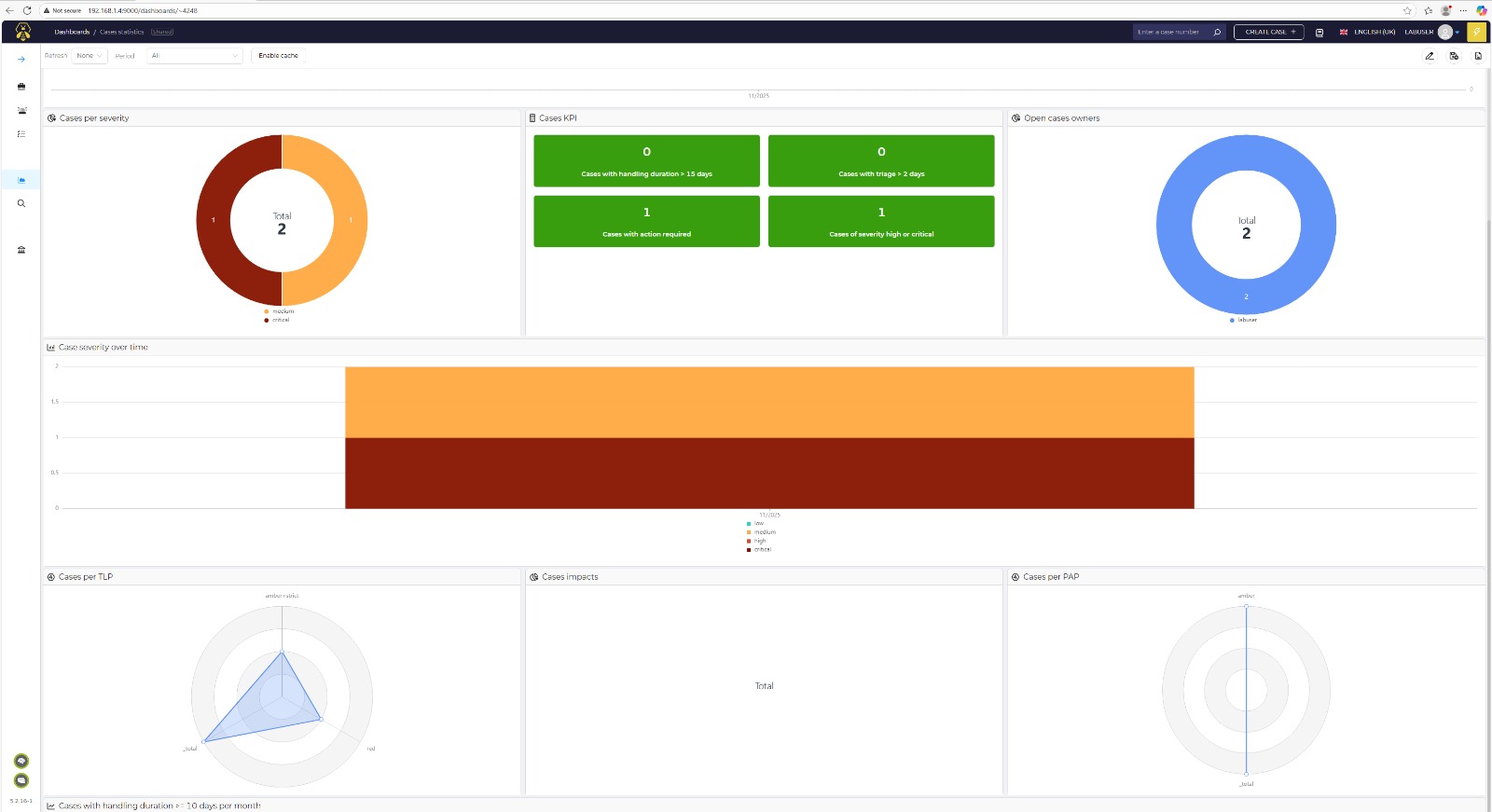
The Incident Simulation (Zero-Day)
I simulated a Critical Zero-Day Intrusion alert to test the workflow.
- The Trigger: A suspicious file hash and external IP (
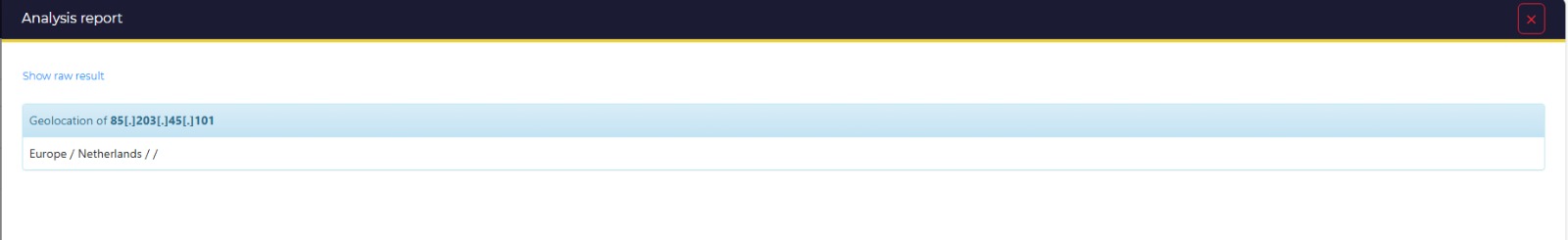
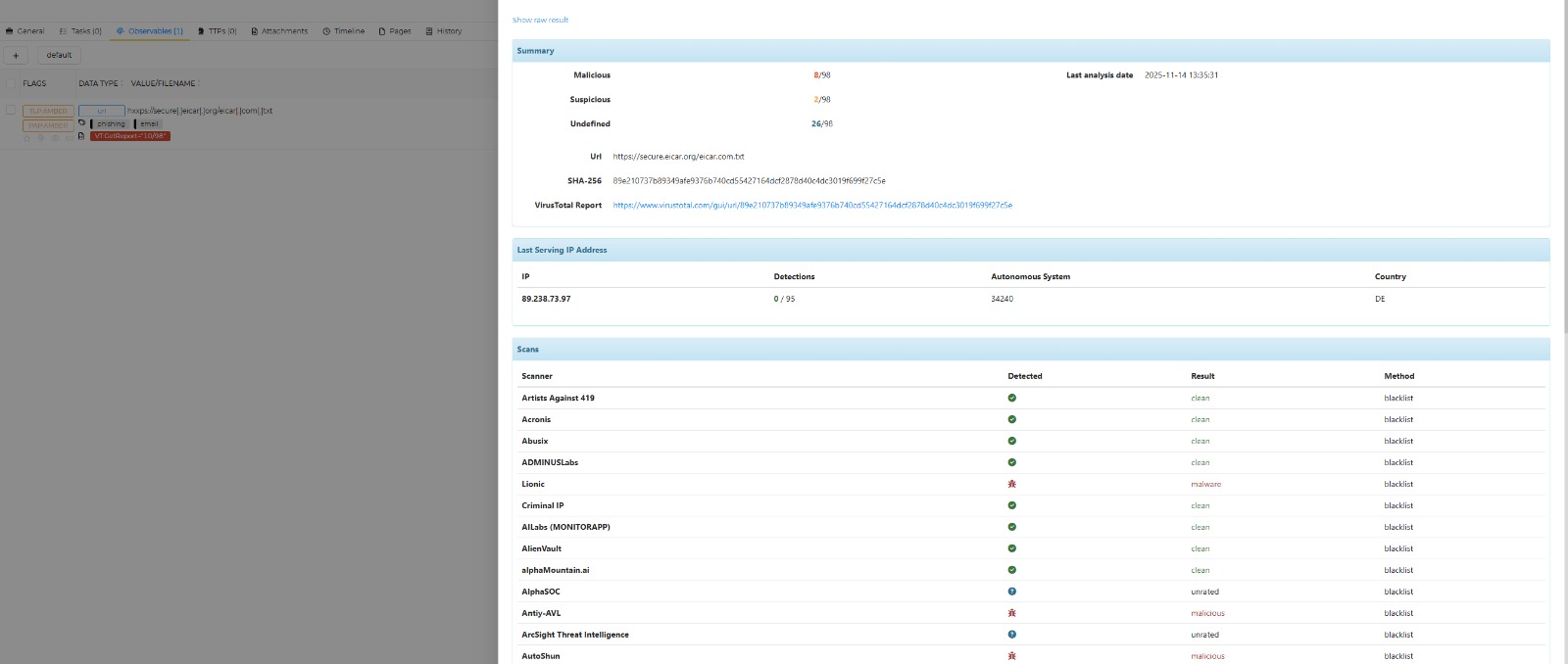
85.203.45.101) were detected. - The Investigation: Instead of manually checking VirusTotal, I triggered Cortex Analyzers directly within the case.
- The Pivot: Cortex returned a ‘Benign’ status for the hash, and GeoIP placed the server in a generic Netherlands cloud host.
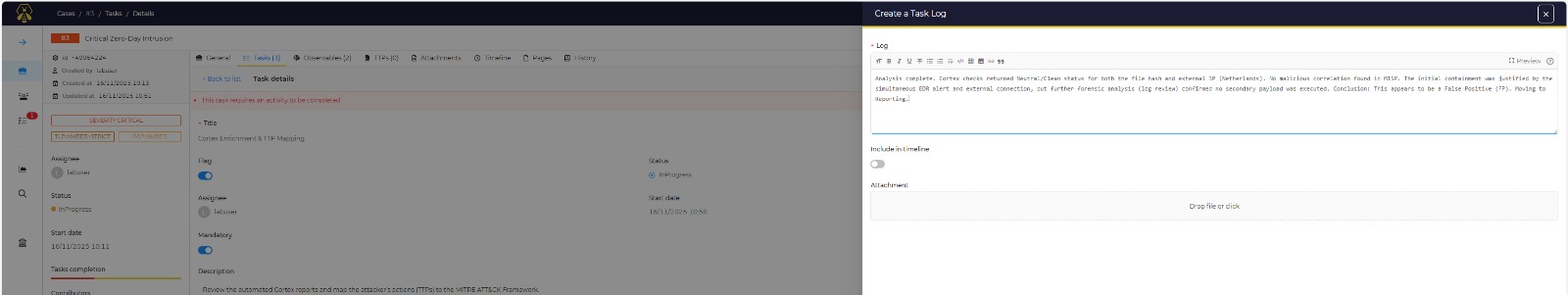
- The Verdict: I identified this as a False Positive. I logged the decision, closed the case, and shared the benign indicators via MISP to prevent other analysts from wasting time on the same alert.
Critical Analysis
While TheHive excels at orchestration, its native reporting capabilities are basic compared to commercial tools like Splunk. For a production environment, I recommend integrating it with Grafana for executive dashboards.





Leave a Reply